https://ninhouston.netlify.app/pandora-hack-on-laptop-mac.html. Mar 27, 2019 The app is compatible with the popular operating systems that includes, iOS, Android, and Mac OS X. Pandora one APK provides one of the fastest and easy ways to download music. Once the search results are generated, Pandora APK one offers the.
Type : Tutorial
Hack RUN for Mac, free and safe download. Hack RUN latest version: Retro amateur hacking game. Hack RUN is a fun hacking game where you have to hack into a mysterious organization to uncover i. Apr 08, 2013 Download Hack RUN for macOS 10.10 or later and enjoy it on your Mac. Ever wanted to be a hacker? Play Hack RUN! Hack your way into the heart of a mysterious organization to uncover their secrets. Hack RUN® is a game which uses 'old school' command prompts (like DOS or UNIX) that simulate a real operating system. May 18, 2017 Download Hack RUN 5.0 for Mac from our website for free. This Mac download was checked by our built-in antivirus and was rated as malware free. The program lies within Games, more precisely Puzzle. You can launch this application on Mac OS X 10.7 or later. Hack run download mac.
Just download the app, and crack networks with vulnerabilities.This app actually targets those networks which are easily vulnerable using some of the default PIN combos. Create new wifi network mac. Most probably you will be successful as this app supports maximum no. Using this app is as simple as it looks. Of routers and that increases your probability of successfully breaking into a WiFi network.
Level : Easy
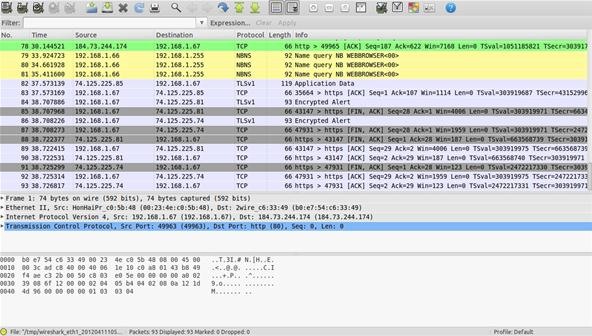
Apr 20, 2016 Wireshark Hacking tutorial: Wireshark is a complete package filled with network analysis tools. Wireshark is not only a packet sniffer but also a packet analyzer, password hacker, and a firewall. It can also detect any denial of service attack on your network and can identify possible hacker.
Last week I'm posting an article about How to Hack Windows via vulnerability in Wireshark, and someone drop a comment and asking about how to detect if someone using wireshark in his network?.
Actually there's a little way you can do when someone using Wireshark in a network, because wireshark only collecting packet data in a passive mode or let's say it's just collecting and grabbing the data that came across the network.
This Wireshark will works perfectly on network that using WI-FI and HUB because the packet that sent and received also sent to another computer inside the network. If you still can't get what I mean, please see the illustrations below.

Hub :
When you're using HUB, the data that sent inside and outside the network will came through HUB, but the main problem is HUB will forward all packet into whole network and check is someone own the packet or not. If there's a computer own the packet, then it will ACCEPT it and the other will DROP the packet.
By using this method, all computer in your network absolutely will receive the packet but they drop it because the packet was not addressed to them. In this network Wireshark will act as data collector and grab all the data even the data was not addressed to them.
Wireless(Wi-Fi) :
This also happen the same in Wi-Fi networks. Wi-fi have the same behavior with HUB, because when you send a packet inside a wireless network, the access point will broadcast your packet to whole network even to your own PC.
But with this kind of network doesn't mean that all wi-fi network can sniff easily, because it was also depend on how the administrator set up and configuring their network.
In this type of network, Wireshark will also act as data collector across the network(esp. on network that didn't have dataencryption).
The Little Way :
When most system attempt to sniff the network their network cards run in promiscious mode. What does promiscious mode mean? according to Wikipedia :
'Promiscuous mode is a configuration of a network card that makes the card pass all traffic it receives to the central processing unit rather than just packets addressed to it — a feature normally used for packet sniffing.'
So if know that promiscuous mode is used for sniffing and if you're attempting to control your local network, you're going to want to know which systems are sniffing on the network so lets find out who's running in promiscuous mode. There are a ton of tools out there to just detect promiscuous mode but now we will use Nmap.
You can edit it in order to achieve a higher standard.The Icon Kit is a feature that allows players to change their appearance in,. Unlock all icons hack geometry dash 2.11 steam mac. This article is currently undergoing development and its information may not be complete. A series of icon designs can be selected for each form as well as corresponding primary and secondary colours, although these are applied to all forms and cannot be selected individually.
Enjoy How to Hack BTD5 on Mac 2017 NEW. Be sure to subscribe!!! Hack btd5 mac. We are not responsible for any illegal actions you do with theses files. All files are uploaded by users like you, we can't guarantee that How to Hack BTD5 on Mac 2017 NEW are up to date. Check out our Instagram, Twitter & Website.How to Hack BTD5 on Mac 2017 NEWHow to install:- Download, extract and run.exe file,(If your antivirus blocking file, pause it or disable it for some time.) - Choose destination folderHow to Use:Open destination folder and locate file notes.txt, open it and read step by step.Enjoy!Don't forget to read instructions after installation.
We can see that the system has been detected to be running in promiscuous mode and the result is '11111111.' Different operating systems report different combinations of 1's. Linux reports '11111111', Windows 2k, XP, Vista, and Windows 7 reports '111___1_'. By default, the script will only report NICs Likely in promiscuous mode so if you don't see get any results, that's because the scan returned false.
Countermeasure :
I think detecting a sniffer was not a good way to control your network, you only caught the suspecting devices after they doing sniffing your network a.k.a it was too late.
And maybe it was better if you do preventive action for your network. Below was the way to prevent as I think(you can add other suggestion for me to put in this article) :
1. Host to host encryption (IPSEC)
Download Wireshark For Mac
2. Use encrypted protocols (SSL,FTPS,SSH)
3. Use switch for your network
Hope it's useful 🙂
Share this article if you found it was useful:
Blogger at hacking-tutorial.com. Love PHP, offensive security and web. Contact him at me[-at-]vishnuvalentino.com
Wireshark Mac Spoofing Hack Wifi Download
See all posts by Vishnu Valentino || Visit Website : http://www.vishnuvalentino.com