It depends on the WiFi encryption type. If it's WPA/WPA2, start here. If it's WEP, start here. Basically, all you need is the MAC address when it comes to cracking WiFi passwords, but once you have control over the router, then knowing the IP is simple and important. Oct 23, 2019 If the hacker is simply looking to access a free Wi-Fi connection, your only sign may be a foreign IP address listed on your network and slower speeds than usual. How to fix a hacked router If the hacker’s intent is more malicious, you may notice more blatant symptoms like unexpected software installations and inaccessible router settings.
Theway a home network usually works is that anyone with your network passphrasecan connect to your home network. However, it’s possible to add another layerof security where only specific devices are allowed to connect. This is calledMAC address filtering.
Keepin mind however that Mac address filtering isn’t a single security solution. Itonly serves as an extra level of difficulty for hackers. It’s a layer that theywill still be able to break through (see below), but anything that makes thingsmore difficult for hackers is always a good thing.
Why Whitelist Devices?
Yourrouter handles all network traffic inside and outside your home network. Itdecides whether certain devices are allowed to connect to your home network.
Normally,this access is determined by whether or not the user of the device types in thecorrect network passphrase. This is the passphrase you configure in the Set Password section under the Security menu in your router.
This is the only security barrier stopping a hacker from connecting to your network. If you’ve set up a complex password, that may be enough. Unfortunately, most people set password that are fairly easy to crack using basic hacker tools.
Youcan add a second layer of security by only allowing specific devices to connectto your home network.
How MAC Address Filtering Works
Youcan set up your router to only allow specific devices by adding their MACaddresses to the router’s Access Control list.
- Usually, you can find thislist by logging into your router and navigating to the Security menu. You’ll find the list of devices under Access Control.
- You can enable the MacAddress Filtering feature by selecting Turnon Access Control.
- Once this is enabled, you canthen select Block all new devices fromconnecting.
- Once this is selected, you’llbe able to select any of the already-connected devices and block them if youdon’t recognize them.
- It’s a good idea while you’redoing this to scan through the devices and make sure all of the listed devicesand MAC addresses are devices you recognize.
- If, later on, you need to addnew devices to the list, you’ll need to change the setting back to Allow all new devices to connect. Thenconnect the device to the network using the network password.
- Once connected, go back tothe Access Control settings and change the setting back to Block all new devices from connecting.
Somerouters will let you enter devices and MAC addresses manually. But to do this,you’ll need to know the MAC address of the computer you’re connecting.
How To Identify The Mac Address Of Your Computer
Checkingthe Mac address on a Windows system is very easy.
- Open the Windows Commandwindow, type ipconfig /all and pressEnter.
- Search through the resultsfor the network adapter that shows as being connected to a network.
- Make a note of the Physical Address listed in thatsection.
- This physical address is thesame as the connected MAC address shown in your router.
On aMacOS system, the process is slightly different.
- Open System Preferences and select Network.
- Select the connected networkand select the Advanced button.
- Select the Hardware tab to see the MAC Address listed at the top.
You can see the procedures above for finding a MAC address on a PC or a Mac, or even on other devices, complete with screenshots and additional details, in this guide on how to determine a MAC address.
Fordevices like Google Home, Alexa, Philips Hue lights, or other smart homedevices, you can usually find the MAC address printed on the label underneaththe device. This is usually the same label where you’d find the serial number.
Onceyou have the MAC addresses for all of the devices that need to whitelist, youcan then log into the router and either make sure they’re already connected, oradd the MAC address to the existing list.
How Hackers Beat MAC Address Filtering
There are a lot of ways hackers can break through your various tactics to secure your Wi-Fi and home network. Hackers also have a way to get through MAC address filtering as well.
Once a hacker recognizes that they’re blocked from accessing your network via MAC address filtering, all they have to do is spoof their own MAC address to match one of the addresses you’ve allowed.
Theydo this by:
- Going into Network and Sharing Center in theControl Panel.
- Selecting Change adapter settings.
- Selecting the Properties of their network adapter andthe Configure button.
- Selecting Network Address and filling in the Value field with the desired MACaddress.
That’sthe easy part. The difficult part is that the hacker will also need to use apacket sniffing tool to pull existing MAC addresses currently communicating onyour network. These software tools are not always easy for amateurs to use, andcan take effort to use correctly.
Othertech sites may tell you that since hackers can do this, then it’s not worthusing MAC address filtering at all. But that’s not entirely true. If you don’tuse MAC address filtering:
- You aren’t even blockingnon-hackers or amateur Wi-Fi thieves from your network.
- You’re avoiding an easy layerof security for no good reason.
- You aren’t trying to makegetting onto your network as difficult as possible with multiple layers ofcomplexity.
- You won’t have access to asimple tool that can help with parental internet controls.
Hacker Need Mac Address Of Router Address
Thisis why it’s a good extra layer of protection for your network, but youshouldn’t depend on it as your only source of protection. Whitelisting specificdevices should be used as just one part of your overall arsenal of networkprotection.
I am going to expose an important topic on hacking knowledge that some of you might know and most of you don’t. When you’re going to hack a computer or server on the Internet, you won’t want your IP address to spill out. That’s because your ISP could easy trace you by two simple information which is the time and IP Address. So you’ll need to use proxy or even chains of proxies to avoid being directly traced by the victim’s firewall. If you think you’re safe hiding behind a proxy server, bad news is most proxy server has logging enabled and your IP address is definitely listed in the log file when you’re connected to it. It is possible that the administrator of the proxy server passes your information to your ISP and you’ll still get caught at the end of the day. Don’t forget, there are still some other important information that can be obtained from an IP Address if a person knows what tools to use. One of it is your network adapter’s MAC address.
Every network card contains a unique code called MAC address that is permanently assigned to it, similarly like every computer requires a unique IP address to be connected to a network. Although these information can be configured to have the same, it would cause conflict and connection problems. To view your network card’s MAC address, just run the command “ipconfig /all” in command prompt and refer to the value of Physical Address.One thing you should know is the MAC address on your computer’s network card will not get passed out to the Internet so there is no way a website or an Internet server can capture this information. Only your Internet Service Provider (ISP) can detect the MAC address of your modem or router. So basically your ISP is capable of tracking your location by your IP address, time and the MAC address of your modem or router.
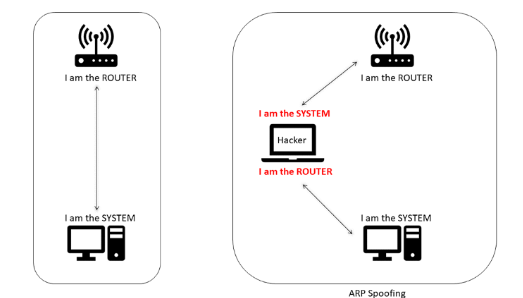
In another scenario, some people may still be using WEP encryption for their wireless network because some old devices don’t support WPA. WEP encryption is very weak and can be cracked in less than 5 minutes using BackTrack Linux. Most of the time they’d also enable a second line of defense which is the MAC address filtering to only allow authorized devices to connect to their wireless network but they’re wrong. A hacker can easily find out the authorized MAC address, change their network card’s MAC address to the authorized ones and poison the ARP cache to prevent the owner’s machine from connecting to it. Here’s an example of Belkin Play Max F7D4401 v1 router. It has a MAC Address Filtering feature where you can set up a list of allowed clients and use the wireless connection.
Other than that, some time limited shareware such as Hotspot Shield that uses your MAC address to keep track of the free usage. If the trial period has expired or is pending to reset every month, you can easily bypass this restriction by changing your MAC address. I bet by now you should know the power of spoofing your MAC Address. MAC address can actually be changed directly from Windows but the easiest way is to just a free program called Technitium MAC Address Changer.
To change your MAC address, run the program, click the Random MAC Address button followed by the Change Now! button. The update takes effect immediately without a reboot and stays intact even when you boot up the computer tomorrow. To restore back your original MAC address, click the Restore Original button on Technitium MAC Address Changer program.
Download Technitium MAC Address Changer
To manually change your MAC address in Windows 7 without using a third party software, go to Control Panel > System > Device Manager. Expand Network Adapters and double click on the network card that you want to change the MAC address. Go to Advanced tab and look for Network Address in the Property box. Click on it and you can specify your own value with any random 12 characters of letters and numbers.
You might also like:
5 Steps to Investigate and Report Abusive IP Address5 Ways to Protect Your Computer Against NetCut’s ARP Spoofing AttackHacker Need Mac Address Of Router Password
4 Ways to Edit URLs at Internet Explorer Address Bar HistoryFind Mac Address Of Router
7 SMTP Providers to Hide Sender IP Address in Email HeadersGet SMS Notification when Electricity Power Supply is RestoredRouter Mac Address Setting
The Technicium Mac address changer has certain restriction in some cases (particularly Wireless connection) such that we should use only ’02’ as fist octet of mac address (as you can see a checkbox in the tool). So, it seems it is not possible to completely spoof your mac address as another PC’s mac address. May be we can play with, by just hiding behind some random mac address.
Replyspoofing the MAC randomly every few minutes may be more useful.
ReplyGet Mac Address Of Router
If you’re behind a router, your ISP only sees the router’s MAC addy. That’s the one you should change.
Regardless, if you have a home broadband connection, you might have a hard time arguing with your ISP since they tie your IP to the modem id.